Securing shared hosting is crucial in today’s digital landscape, where cyber threats are on the rise. With the increasing popularity of shared hosting services, it is important to understand how to protect your website and data from potential security vulnerabilities. Sharing server resources with other websites can expose your site to various risks, but with proper security measures in place, you can minimize the chances of an attack and safeguard your online presence.
One of the key aspects of securing shared hosting is ensuring that your provider has robust security protocols in place. Look for hosting providers that offer regular security updates, firewalls, malware scanning, and backup services. Additionally, it is essential to keep your website’s software up to date, including the content management system (CMS) and any plugins or themes you have installed. Regularly monitoring your website for vulnerabilities and conducting security audits can also help identify and address potential risks before they become major security concerns.
If you’re looking to secure your shared hosting, follow these essential steps:
- Keep your software up to date by regularly installing updates and patches.
- Create strong passwords for all accounts associated with your hosting.
- Enable two-factor authentication for added security.
- Regularly backup your data to a secure location.
- Implement a reliable firewall and use encryption for sensitive data.
Introduction to Securing Shared Hosting
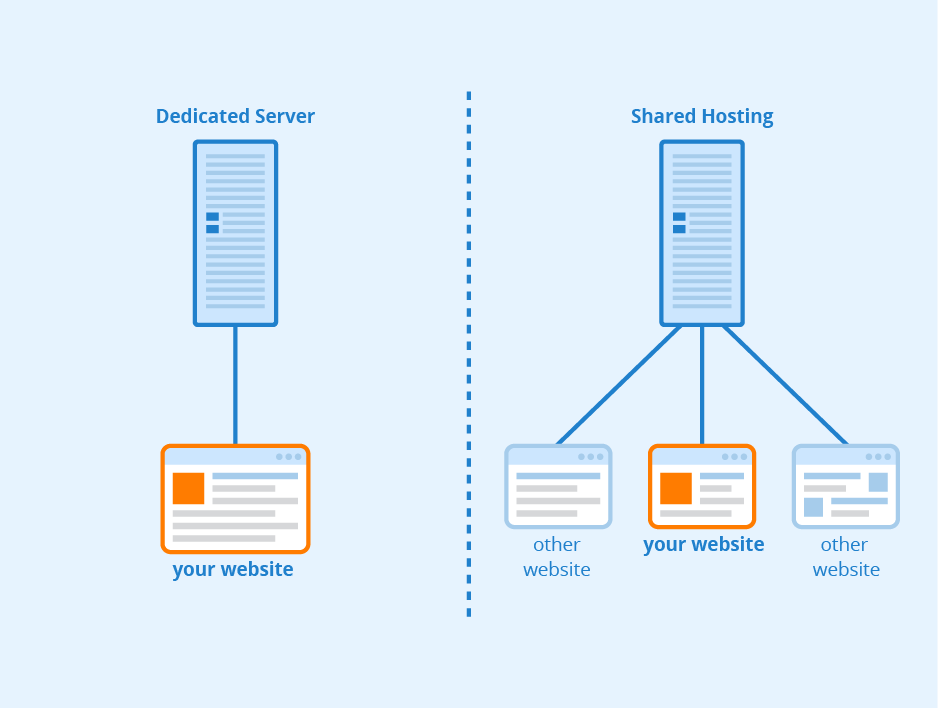
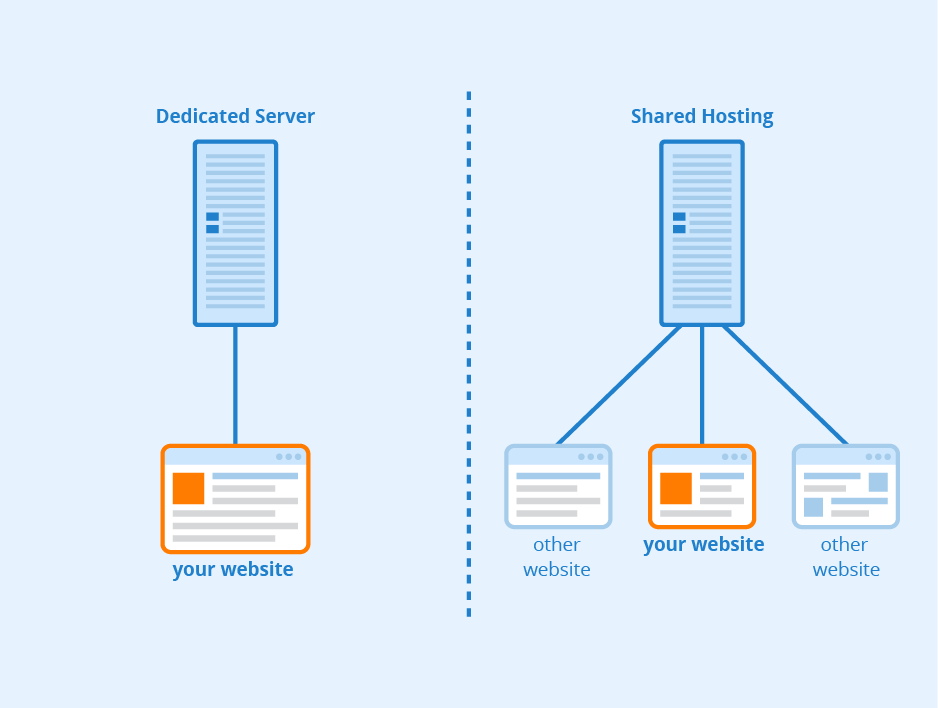
Shared hosting is a popular option for individuals and small businesses looking to establish an online presence. With shared hosting, multiple websites share resources on a single server, making it a cost-effective solution. However, security is a crucial aspect that must be taken into consideration when using shared hosting. This article will explore various strategies and best practices to secure shared hosting and protect websites from potential threats.
When it comes to securing shared hosting, there are several key areas to focus on. These include securing user accounts, protecting against malware and viruses, securing the server environment, and implementing regular backups. By addressing these aspects, website owners can significantly enhance the security of their shared hosting environment and ensure the safety of their data.
One essential step to secure shared hosting is to secure user accounts properly. Each website hosted on a shared server has its own FTP account, control panel access, and email accounts. It’s crucial to enforce strong passwords for these accounts and educate users about password security best practices. Additionally, limiting the number of users with administrative privileges and regularly monitoring account activity can help prevent unauthorized access and potential security breaches.
For more advanced security measures, website owners can implement two-factor authentication (2FA) for user accounts. 2FA adds an extra layer of security by requiring users to provide additional verification, such as a temporary code sent to their mobile device, in addition to their password. This can significantly reduce the risk of unauthorized access to user accounts and sensitive information.
Securing Against Malware and Viruses
Malware and viruses pose significant threats to shared hosting environments, as their presence can lead to website defacement, data breaches, and the spread of malicious content. To protect against malware and viruses, it is essential to take proactive measures and establish a robust security framework.
Implementing a reliable antivirus software solution is a crucial step in securing shared hosting. The antivirus software should be capable of scanning for malware, viruses, and other malicious files on a regular basis. It should also provide real-time protection to detect and prevent any potential threats from infiltrating the system.
In addition to antivirus software, website owners should also consider implementing a web application firewall (WAF). A WAF acts as a protective barrier between the website and the internet, filtering out malicious traffic and preventing attacks such as SQL injections and cross-site scripting (XSS) attacks. It continuously monitors and blocks suspicious activities, providing an extra layer of security for the shared hosting environment.
Regularly updating and patching all software and scripts used on the shared hosting environment is essential to avoid vulnerabilities that can be exploited by malware and viruses. This includes the server operating system, content management systems (CMS), plugins, and themes. Outdated software can often have security vulnerabilities that can be easily targeted by hackers. By keeping everything up to date, website owners can significantly reduce the risk of malware infections and security breaches.
Implementing Secure Coding Practices
In addition to securing the hosting environment, website owners must also take measures to ensure the security of their website’s code. Implementing secure coding practices can help mitigate the risk of common vulnerabilities and protect against attacks.
One essential practice is to sanitize and validate all user input to prevent malicious code injection. This involves filtering and validating any data received from users before processing it on the server. By doing so, website owners can prevent vulnerabilities such as SQL injections and cross-site scripting attacks.
Another vital practice is to regularly scan the website’s source code for any security vulnerabilities. Various tools and services can help identify common coding mistakes and vulnerabilities that can be exploited by attackers. By conducting regular code audits, website owners can identify and address any potential weaknesses in the website’s code before they are exploited.
Implementing secure coding practices is an ongoing process that involves staying updated with the latest security best practices and following secure coding guidelines. Regularly educating developers about secure coding practices helps ensure that the website’s code remains robust and can withstand potential attacks.
Regular Server and Application Monitoring
Regular monitoring of the server and applications hosted on the shared hosting environment is essential to detect any potential security issues or unusual activities. This includes monitoring server logs, network traffic, and application logs.
Monitoring server logs can help identify any suspicious activity or unauthorized access attempts. By reviewing the logs regularly, website owners can detect any potential security breaches and take appropriate action to mitigate them.
Network traffic monitoring helps identify any unusual patterns or malicious traffic that could signify a security threat. It can help identify distributed denial-of-service (DDoS) attacks or attempts to exploit vulnerabilities in the network infrastructure.
Lastly, application logs provide valuable information about the functioning of the website and can help identify any abnormal behavior or potential security issues within the applications. Regularly reviewing application logs can help detect and address security vulnerabilities before they are exploited.
Securing the Server Environment
Securing the server environment is paramount when it comes to shared hosting. Since multiple websites share resources on a single server, a compromise in one website’s security can potentially affect other websites hosted on the same server.
One of the first steps in securing the server environment is to choose a reputable hosting provider that prioritizes security. Reputable hosting providers often implement robust security measures and regularly update their server software to protect against potential vulnerabilities.
Additionally, website owners should consider enabling server-level security features such as Secure Sockets Layer (SSL) certificates for secure data transmission and Secure Shell (SSH) access for encrypted and secure remote server administration.
Apart from these, employing strict file and directory permissions is crucial to prevent unauthorized access to sensitive data or critical system files. It’s important to ensure that only necessary permissions are granted, and unnecessary write or execute permissions are revoked.
Regular Backups
Regular backups of the website’s files and databases are essential to ensure quick recovery in case of a security breach or data loss. Website owners should consider taking regular backups and storing them separately from the shared hosting environment.
Cloud-based backup solutions are often a reliable option as they offer off-site storage and redundancy. It’s advisable to automate the backup process to ensure regular and consistent backups are taken without manual intervention.
Disaster Recovery Plan
Having a robust disaster recovery plan is crucial to minimize the impact of any security breaches or server failures. The plan should include steps to restore the website from backups, implement necessary security patches, and notify appropriate stakeholders about the incident.
Regularly testing the disaster recovery plan and updating it based on any changes in the shared hosting environment or website structure is essential. This ensures that the plan remains effective and can be easily implemented in case of an actual security incident.
Conclusion
Securing shared hosting is vital to protect websites and their data from potential threats. By following best practices and implementing effective security measures, website owners can enhance the overall security of their shared hosting environment.
Securing user accounts, protecting against malware and viruses, securing the server environment, and implementing regular backups are key areas that website owners need to focus on. Additionally, implementing secure coding practices and regularly monitoring the server and applications can significantly bolster the security of the shared hosting environment.
Remember, maintaining a secure shared hosting environment is an ongoing process that requires vigilance and regular updates. By prioritizing security and staying updated with the latest security practices, website owners can protect their websites and ensure the safety of their data.
Key Takeaways: How to Secure Shared Hosting?
- Keep your software and scripts up to date to patch any security vulnerabilities.
- Use strong and unique passwords for all your accounts.
- Regularly backup your website to ensure you can recover in case of any security incidents.
- Install a reliable security plugin to add an extra layer of protection to your website.
- Limit file and directory permissions to prevent unauthorized access.
Securing shared hosting is crucial to protect your website and data. Here are some key steps:
- Use a strong and unique password for your hosting account.
- Regularly update your website’s software and plugins.
- Install a reliable security plugin to scan and monitor your website.
- Enable SSL/TLS encryption to secure data transmission.
- Back up your website and database regularly.
Following these steps will help safeguard your shared hosting and keep your website safe.